In 2021, I wrote about how offensive actors can leverage AWS SSO device code for phishing, rendering modern security controls like FIDO authentication or identity provider device posture ineffective: Phishing for AWS credentials via AWS SSO device code authentication. In this post, we’ll take a closer look at the newly-released PKCE support for AWS SSO authentication flows. A Short History of Device Code Phishing As highlighted in the original article, Device Code phishing isn’t new or specific to AWS. In fact, it had previously been demonstrated in the context of Azure AD. However, following the publication, the technique gained notableContinue reading… The New PKCE Authentication in AWS SSO Brings Hope (Mostly)
Stop worrying about ‘allowPrivilegeEscalation’
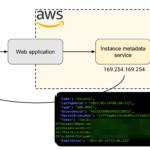
IMDSv2 enforcement: coming to a region near you!
A Tribute to Hadrien Milano
MitM at the Edge: Abusing Cloudflare Workers
Introducing Stratus Red Team, an Adversary Emulation Tool for the Cloud
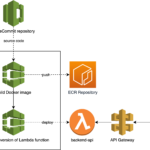
Implementing a Vulnerable AWS DevOps Environment as a CloudGoat Scenario
I’m a huge fan of disposable security labs, both for offensive and defensive purposes (see: Automating the provisioning of Active Directory labs in Azure). After writing Cloud Security Breaches and Vulnerabilities: 2021 in Review, I wanted to build a “purposely vulnerable AWS lab” with a typical attack path including static, long-lived credentials and with a supply-chain security element.
Cloud Security Breaches and Vulnerabilities: 2021 in Review
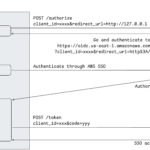
Phishing for AWS credentials via AWS SSO device code authentication (updated 2024)
When using AWS in an enterprise environment, best practices dictate to use a single sign-on service for identity and access management. AWS SSO (newly referred to as “Identity Center”) is a popular solution, integrating with third-party providers such as Okta and allowing to centrally manage roles and permissions in multiple AWS accounts. In this post, we demonstrate that AWS SSO is vulnerable by design to device code authentication phishing – just like any identity provider implementing OpenID Connect device code authentication. This technique was first demonstrated by Dr. Nestori Syynimaa for Azure AD. The feature provides a powerful phishing vectorContinue reading… Phishing for AWS credentials via AWS SSO device code authentication (updated 2024)