In this post, we take a look at an anti-forensics technique that malware can leverage to hide injected DLLs. We dive into specific details of the Windows Process Environment Block (PEB) and how to abuse it to hide a malicious loaded DLL.
Category: Windows Security
Automating the provisioning of Active Directory labs in Azure
Today, I’m releasing Adaz, a project aimed at automating the provisioning of hunting-oriented Active Directory labs in Azure. This post is the making of, where we walk through how to leverage Terraform and Ansible to spin up full-blown Active Directory environments with Windows Server 2019 and Windows 10 machines.
Hidden in PEB Sight: Hiding Windows API Imports With a Custom Loader
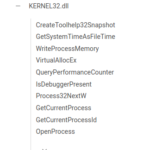
In this post, we look at different techniques to hide Windows API imports in a program in order to fly under the radar of static analysis tools. Especially, we show a method to hide those imports by dynamically walking the process environment block (PEB) and parsing kernel32.dll in-memory to find its exported functions. Let’s dive in!
Stealthier persistence using new services purposely vulnerable to path interception
Building an Office macro to spoof parent processes and command line arguments
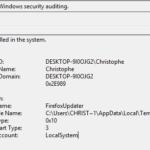
Most modern EDR solutions use behavioral detection, allowing to detect malware based on how it behaves instead of solely using static indicators of compromise (IoC) like file hashes or domain names. In this post, I give a VBA implementation of two techniques allowing to spoof both the parent process and the command line arguments of a newly created process. This implementation allows crafting stealthier Office macros, making a process spawned by a macro look like it has been created by another program such as explorer.exe and has benign-looking command line arguments. I am not the author of these techniques. CreditsContinue reading… Building an Office macro to spoof parent processes and command line arguments