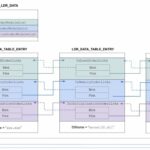
In this post, we take a look at an anti-forensics technique that malware can leverage to hide injected DLLs. We dive into specific details of the Windows Process Environment Block (PEB) and how to abuse it to hide a malicious loaded DLL.
Tag: malware
Set up your own malware analysis lab with VirtualBox, INetSim and Burp
In this post we will set up a virtual lab for malware analysis. We’ll create an isolated virtual network separated from the host OS and from the Internet, in which we’ll setup two victim virtual machines (Ubuntu and Windows 7) as well as an analysis server to mimic common Internet services like HTTP or DNS. Then, we’ll be able to log and analyze the network communications of any Linux or Windows malware, which will unknowingly connect to our server instead of the Internet. We demonstrate the setup with a real life use case where we analyze the traffic of the infamous TeslaCrypt ransomware, a now defunct ransomware which infected a large number of systemsContinue reading… Set up your own malware analysis lab with VirtualBox, INetSim and Burp