Today’s post is unlike any I ever wrote: a tribute to a dear friend, who, a few months ago, brutally passed away from a heart attack at the age of 28.
Category: Uncategorized
MitM at the Edge: Abusing Cloudflare Workers
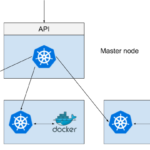
They told me I could be anything, so I became a Kubernetes node – Using K3s for command and control on compromised Linux hosts
In their RSA 2020 talk Advanced Persistence Threats: The Future of Kubernetes Attacks, Ian Coldwater and Brad Geesaman demonstrated that K3s, a lightweight version of Kubernetes, can be used to backdoor compromised Kubernetes clusters. This post describes how K3s can also serve as an easy command and control (C2) mechanism to remotely control compromised Linux machines.
Quickly access your configuration files on your server
It’s been a while since I last wrote a post on this blog, so I’ve decided to share a simple way to quickly access the configuration files of the numerous services you may be running on your server. It is indeed quite painful to frequently edit arbitrary deep configuration files (such as /etc/php5/apache2/php.ini) that are spread out in your file system and which you don’t remember the names. The trick I am using is a directory named cfg at the root of my server, in which I create symbolic links pointing to configuration files or directories containing them, with names that are easier to remember.