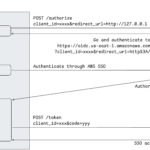
In 2021, I wrote about how offensive actors can leverage AWS SSO device code for phishing, rendering modern security controls like FIDO authentication or identity provider device posture ineffective: Phishing for AWS credentials via AWS SSO device code authentication. In this post, we’ll take a closer look at the newly-released PKCE support for AWS SSO authentication flows. A Short History of Device Code Phishing As highlighted in the original article, Device Code phishing isn’t new or specific to AWS. In fact, it had previously been demonstrated in the context of Azure AD. However, following the publication, the technique gained notableContinue reading… The New PKCE Authentication in AWS SSO Brings Hope (Mostly)
Category: Cloud Security
IMDSv2 enforcement: coming to a region near you!
Introducing Stratus Red Team, an Adversary Emulation Tool for the Cloud
Implementing a Vulnerable AWS DevOps Environment as a CloudGoat Scenario
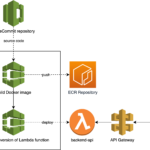
I’m a huge fan of disposable security labs, both for offensive and defensive purposes (see: Automating the provisioning of Active Directory labs in Azure). After writing Cloud Security Breaches and Vulnerabilities: 2021 in Review, I wanted to build a “purposely vulnerable AWS lab” with a typical attack path including static, long-lived credentials and with a supply-chain security element.
Cloud Security Breaches and Vulnerabilities: 2021 in Review
Phishing for AWS credentials via AWS SSO device code authentication (updated 2024)
When using AWS in an enterprise environment, best practices dictate to use a single sign-on service for identity and access management. AWS SSO (newly referred to as “Identity Center”) is a popular solution, integrating with third-party providers such as Okta and allowing to centrally manage roles and permissions in multiple AWS accounts. In this post, we demonstrate that AWS SSO is vulnerable by design to device code authentication phishing – just like any identity provider implementing OpenID Connect device code authentication. This technique was first demonstrated by Dr. Nestori Syynimaa for Azure AD. The feature provides a powerful phishing vectorContinue reading… Phishing for AWS credentials via AWS SSO device code authentication (updated 2024)
Retrieving AWS security credentials from the AWS console
Shifting Cloud Security Left — Scanning Infrastructure as Code for Security Issues (last updated August 2023)
In cloud environments, companies usually describe their infrastructure as code using tools like Terraform or CloudFormation. In this post, we review the landscape of tools that allow us to perform static analysis of Terraform code in order to identify cloud security issues and misconfigurations even before they pose an actual security risk.
Privilege Escalation in AWS Elastic Kubernetes Service (EKS) by compromising the instance role of worker nodes
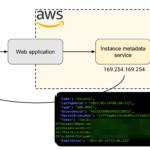
In this post, we discuss the risks of the AWS Instance Metadata service in AWS Elastic Kubernetes Service (EKS) clusters. In particular, we demonstrate that compromising a pod in the cluster can have disastrous consequences on resources in the AWS account if access to the Instance Metadata service is not explicitly blocked. Introduction For the purposes of this post, we’ll use an EKS cluster running Kubernetes v1.17.9 and created with eksctl. We could also have created the cluster using Terraform or CloudFormation. Once we created the cluster, we can use the AWS CLI to update our kubectl configuration file forContinue reading… Privilege Escalation in AWS Elastic Kubernetes Service (EKS) by compromising the instance role of worker nodes
Abusing the AWS metadata service using SSRF vulnerabilities
I recently worked on a small toy project to execute untrusted Python code in Docker containers. This lead me to test several online code execution engines to see how they reacted to various attacks. While doing so, I found several interesting vulnerabilities in the code execution engine developed by Qualified, which is quite widely used including by websites like CodeWars or InterviewCake. The combination of being able to run code with network access and the fact that the infrastructure was running in Amazon Web Services lead to an interesting set of vulnerabilities which we present in this post.