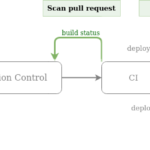
In cloud environments, companies usually describe their infrastructure as code using tools like Terraform or CloudFormation. In this post, we review the landscape of tools that allow us to perform static analysis of Terraform code in order to identify cloud security issues and misconfigurations even before they pose an actual security risk.
Category: Security
Privilege Escalation in AWS Elastic Kubernetes Service (EKS) by compromising the instance role of worker nodes
In this post, we discuss the risks of the AWS Instance Metadata service in AWS Elastic Kubernetes Service (EKS) clusters. In particular, we demonstrate that compromising a pod in the cluster can have disastrous consequences on resources in the AWS account if access to the Instance Metadata service is not explicitly blocked. Introduction For the purposes of this post, we’ll use an EKS cluster running Kubernetes v1.17.9 and created with eksctl. We could also have created the cluster using Terraform or CloudFormation. Once we created the cluster, we can use the AWS CLI to update our kubectl configuration file forContinue reading… Privilege Escalation in AWS Elastic Kubernetes Service (EKS) by compromising the instance role of worker nodes
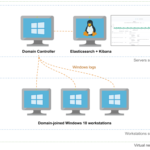
Automating the provisioning of Active Directory labs in Azure
Today, I’m releasing Adaz, a project aimed at automating the provisioning of hunting-oriented Active Directory labs in Azure. This post is the making of, where we walk through how to leverage Terraform and Ansible to spin up full-blown Active Directory environments with Windows Server 2019 and Windows 10 machines.
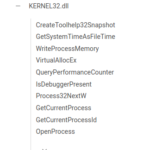
Hidden in PEB Sight: Hiding Windows API Imports With a Custom Loader
In this post, we look at different techniques to hide Windows API imports in a program in order to fly under the radar of static analysis tools. Especially, we show a method to hide those imports by dynamically walking the process environment block (PEB) and parsing kernel32.dll in-memory to find its exported functions. Let’s dive in!
Stealthier persistence using new services purposely vulnerable to path interception
Building an Office macro to spoof parent processes and command line arguments
Most modern EDR solutions use behavioral detection, allowing to detect malware based on how it behaves instead of solely using static indicators of compromise (IoC) like file hashes or domain names. In this post, I give a VBA implementation of two techniques allowing to spoof both the parent process and the command line arguments of a newly created process. This implementation allows crafting stealthier Office macros, making a process spawned by a macro look like it has been created by another program such as explorer.exe and has benign-looking command line arguments. I am not the author of these techniques. CreditsContinue reading… Building an Office macro to spoof parent processes and command line arguments
[Write-up] Insomni’hack 2018 CTF teaser
CloudFlair: Bypassing Cloudflare using Internet-wide scan data
Cloudflare is a service that acts as a middleman between a website and its end users, protecting it from various attacks. Unfortunately, those websites are often poorly configured, allowing an attacker to entirely bypass Cloudflare and run DDoS attacks or exploit web-based vulnerabilities that would otherwise be blocked. This post demonstrates the weakness and introduces CloudFlair, an automated detection tool.
Abusing the AWS metadata service using SSRF vulnerabilities
I recently worked on a small toy project to execute untrusted Python code in Docker containers. This lead me to test several online code execution engines to see how they reacted to various attacks. While doing so, I found several interesting vulnerabilities in the code execution engine developed by Qualified, which is quite widely used including by websites like CodeWars or InterviewCake. The combination of being able to run code with network access and the fact that the infrastructure was running in Amazon Web Services lead to an interesting set of vulnerabilities which we present in this post.
[Write-up] SickOs 1.2
This post is a walkthrough of the VulnHub machine SickOs 1.2. I previously wrote one for its little sister, SickOs 1.1. I found this second version to be more challenging, but also more realistic; the author tried to mimic what one could encounter during a real engagement – and it does it pretty well.


![[Write-up] Insomni’hack 2018 CTF teaser](https://blog.christophetd.fr/wp-content/uploads/2018/01/dedba8bd33cadb8f0e4bac9fb5181111_400x400-150x150.png)


![[Write-up] SickOs 1.2](https://blog.christophetd.fr/wp-content/uploads/2017/06/1497627146_firewall-150x150.png)